- Home
- Information Security
- Product security
Product security
Ricoh’s product security
What is product security?
We call our activities to protect customers' information handled by products and services from attackers “product security.”
The Ricoh Group’s initiatives
The digitalization of aspects of where we live and work has transformed us into an environment where many goods and services are connected. In this environment, increasingly advanced and sophisticated cyber attacks are targeting vulnerable points in the supply chain.
Against this backdrop, the Ricoh Group will design security from the development stage to ensure that customers can use our products and services with confidence. And after their launch, we will continue to work on the following to detect and handle vulnerabilities in a responsible manner.
- ・ Acquire security technologies that keep pace with advances and innovations in digital technology.
- ・ Establish an organization to implement product security.
- ・ Strive to maintain quality related to security by establishing group-wide standards that comply with international standards.
- ・ Develop security-conscious products and services and conduct security verification to prevent the introduction and the leakage of vulnerabilities.
- ・ Collect information on vulnerabilities and take appropriate action when it affects our products and services.
- ・ Provide customers with useful information about the security of our products and services.
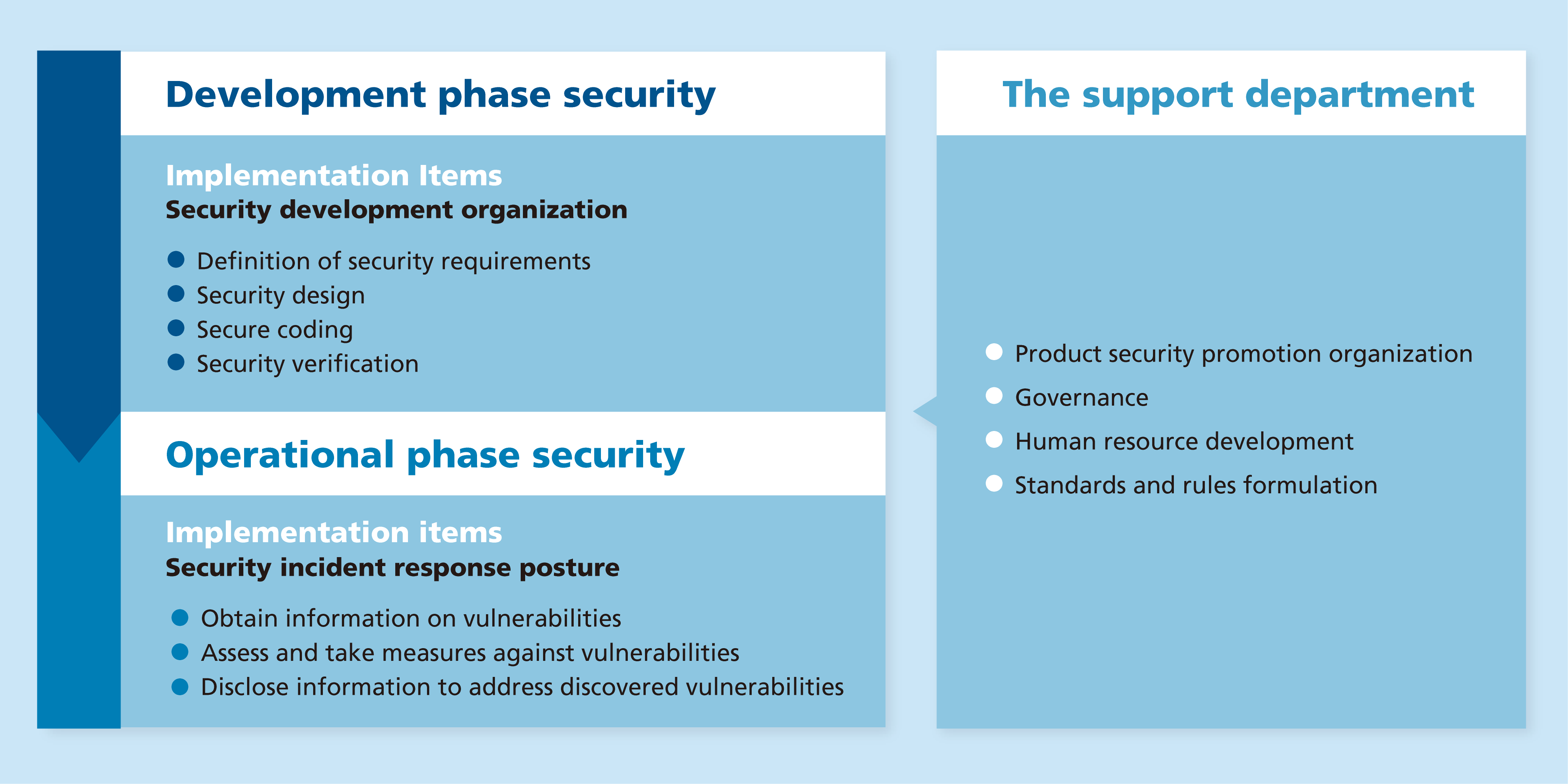
Security policy and initiatives in the development phase
To ensure that customers and users of our products and services can use them with peace of mind, the Ricoh Group will practice security by design based on ISO/IEC 27034-1:2011 (Application security — Part 1: Overview and concepts), which considers security throughout the lifecycle of products and services from the planning and design stages.
Security Development Policy
The Ricoh Group will establish a security development organization and implement measures to prevent the introduction and the leakage of vulnerabilities during the development of products and services.
Prevent the introduction of vulnerabilities
We design security measures to protect against threats to products and services and implement security measures accurately and securely.
Prevent the leakage of vulnerabilities
We conduct vulnerability assessments and take necessary countermeasures when vulnerabilities are found.
Action guidelines for security development
The Ricoh Group will practice and study the following items as Group regulations to prevent the introduction and the leakage of vulnerabilities.
Definition of security requirements
We will determine the information and functions that need to be protected by security, the operational environment in which security measures are to be taken, and the target values for security risk reduction that are compatible with the characteristics of the product or service.
Security design
We will identify threats to information and functions that need to be protected and design security functions and secure operating environments/methods (security measures) to mitigate the occurrence of threats.
Moreover, we will design security functions that counter threats with a program structure and mechanism (security architecture) that does not cause disabling or performance degradation of the function itself.
Secure coding
To avoid introducing vulnerabilities during implementation, we will establish rules for creating secure code and program according to those rules.
The created program will then be subjected to static analysis to confirm that it complies with the rules.
Security verification
We conduct security verification according to the characteristics of the products and services, and take necessary measures if vulnerabilities are found.
Security policy and initiatives in the operation phase
The Ricoh Group will respond to vulnerabilities based on “ISO/IEC 29147 (Vulnerability disclosure)” and “ISO/IEC 30111 (Vulnerability handling process)” for early detection and early response to vulnerabilities that may affect products and services after they are provided to the market. We will also participate in the “Information Security Early Warning Partnership*1” to minimize damage caused by vulnerabilities.
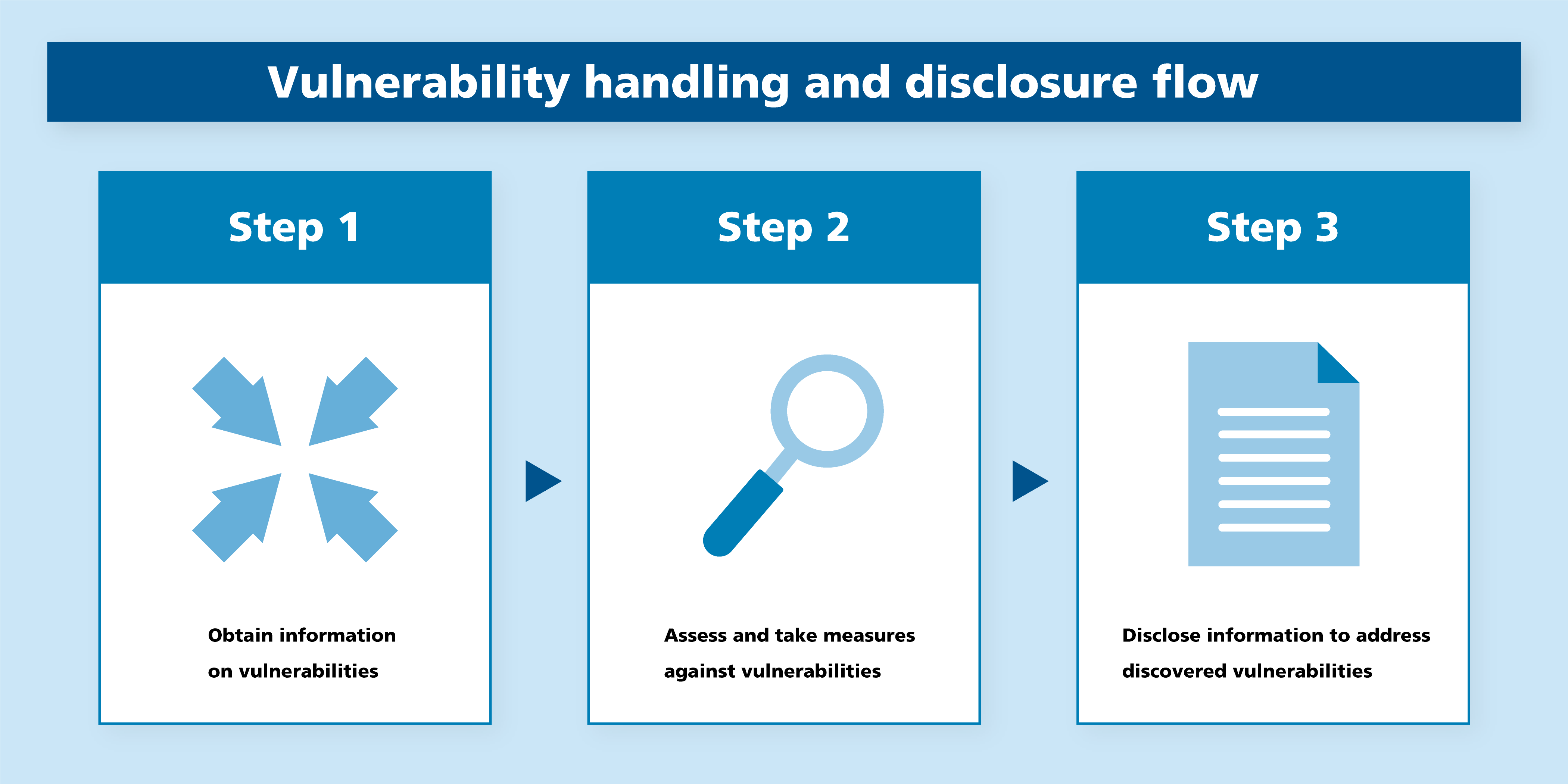
Vulnerability handling and disclosure policy
The Ricoh Group will establish a security incident response posture to ensure that users of our products and services can use those with confidence.
And we will obtain information on vulnerabilities, assess and take measures against those, and disclose information on addressing vulnerabilities.
Obtain information on vulnerabilities
The Ricoh Group will obtain information on vulnerabilities quickly from a broad range of sources inside and outside the Group, and share the information with the development departments that will evaluate and address the vulnerability.
Assess and take measures against vulnerabilities
After evaluating the vulnerability and confirming that the vulnerability affects a product or service, the development department will implement countermeasures and prepare procedures to address the vulnerability for the customer’s product or service.
Disclose information to address discovered vulnerabilities.
The Ricoh Group will disclose as information to address discovered vulnerabilities information on and countermeasures against the vulnerabilities (including workarounds) to those who need such information at the appropriate time in accordance with the "principle of simultaneous disclosure of information on countermeasures*2" and the “principle of consistent disclosure date*3.”
- *2: When information on vulnerability is disclosed, information on countermeasures shall also be provided at the same time. If we disclose information about vulnerabilities before countermeasures are in place, there is a possibility that malicious third parties will develop and distribute attack code to exploit the vulnerabilities, which could then be used to launch cyber attacks against customers.
- *3: In the case of vulnerabilities that also affect the products and services of other companies, information disclosure shall be made with a certain level of coordination among the parties concerned. If we disclose information independently without waiting for the information disclosure date coordinated among concerned parties, that would expose customers who use other companies’ products and services to the risk of cyber attacks.
Action guidelines for vulnerability handling and disclosure
Obtain information on vulnerabilities
The Ricoh Group shall obtain information on vulnerabilities quickly from sources inside and outside the Group, and use a vulnerability management system*4 to evaluate information on vulnerabilities and share that with the development department responsible for countermeasures against vulnerabilities of the product or service.
- ・ Obtain information on vulnerabilities in the Ricoh Group
We will continuously conduct security verification throughout the lifecycle of products and services according to the characteristics of the products and services.
- ・ Obtain information on vulnerabilities outside the Ricoh Group
We will collect information on product vulnerabilities from users of our products and services, security researchers, and organizations that collect and distribute security-related information (such as JPCERT/CC*5).
- *4: The Ricoh Group’s internal system to manage vulnerabilities from obtaining information to completing countermeasures
- *5: Abbreviation for Japan Computer Emergency Response Team Coordination Center JPCERT/CC performs tasks such as collecting computer security information, supporting incident response, and disseminating computer security-related information.
Assess and take measures against vulnerabilities
The product/service development department will evaluate the impact of the vulnerability received in the vulnerability management system on the product/service, and if it is confirmed that the vulnerability affects the product/service, the department will prepare information on and countermeasures against vulnerabilities as information on addressing vulnerabilities after implementing the necessary security measures.
Disclose information to address discovered vulnerabilities.
The Ricoh Group will disclose information on vulnerabilities so that those who need to be informed of the impact on products and services and those who need to address the vulnerabilities will receive that information. The timing of disclosure may be coordinated with JPCERT/CC.
Contacting Ricoh to report vulnerabilities for Ricoh's products and services
If you have discovered a vulnerability in a Ricoh Group product or service, please contact us at the dedicated contact point shown below for any questions or concerns regarding security.
In the case of vulnerability-related information, we will investigate the reported information and inform the person who contacted us of the results of our investigation.
In addition, we may ask the person who reported the information to provide additional information or adjust the date of disclosure as necessary.
Please contact the Ricoh Technical Call Center or a Ricoh representative.
If you are a user of Ricoh Group products or services and have questions or concerns about vulnerabilities in our products or services, please contact the Ricoh Technical Call Center or a sales or service representative.
In case your report is related to a yet undiscovered vulnerability in our products or services, the local service representative will report the response status and progress to those who requests so, until vulnerability countermeasure information is disclosed.
When we begin reporting, the local service representative will provide you with information on how to prevent sensitive data from leaking, so please make sure to follow those instructions. Your cooperation is greatly appreciated.
If you have discovered a vulnerability, please provide us with the following information.
- ・ Name and version of the product or service
- ・ How to reproduce the vulnerability
< If you are using a security, penetration or network scanning tool >
- ・ Name and version of the tool
- ・ Information on the settings of the tool
- ・ Output results of the tool
Please contact us via the Vulnerability Submission Form.
If you are a security researcher and have found a vulnerability in a Ricoh Group product or service, please contact us using the Vulnerability Submission Form provided by Ricoh on our website.
Once we receive your message, we will immediately send you a confirmation email describing your inquiry.
In case your report is related to a yet undiscovered vulnerability in our products or services, we will report the response status and progress, until vulnerability countermeasure information is disclosed.
The submission form is encrypted by SSL/TLS. Communication with the reporting party after the contact by the submission form will be via e-mail.
If you wish to report via email, please use a PGP public key and encrypt the email in order to prevent information leakage during the email transmission.
A PGP public key will be provided separately to those who contact us via the submission form.
Vulnerability Submission Form:
https://webform.ricoh.com/form/pub/e00134/vulnerability_inq_en
Acknowledgment for reporting vulnerabilities
Acknowledgment of those who report vulnerabilities affecting Ricoh Group products and services through the contact point will be posted in the information on addressing vulnerabilities if the person reporting agrees to the posting of the acknowledgment.
If multiple individuals or organizations report the same vulnerability, acknowledgment will be given to the first to report the vulnerability.
Disclosure of information to address discovered vulnerabilities on products and services
The Ricoh Group will disseminate information on addressing vulnerabilities in our products and services to those who need such information.
Information on addressing vulnerabilities that should be widely disclosed will be posted on this web page.





