
- Home
- Information Security
- Information security at the Ricoh Group
- Providing value
- Providing value | Value Provided ISMS Internal Audit Issues
Providing value

Internal audits of the ISMS tend to be a collection of points that are too often nitpicked about in the pursuit of conformance to standards. Of course, auditing for compliance with standards is fundamental, but by taking a step further to auditing for effectiveness, risks that were previously unnoticed can be revealed.
Threats to information assets are related to the operation of information assets (lifecycle), the environment in which information assets are located (facilities), and compliance with laws, regulations, and contracts related to information assets. Risk assessment and internal audits must be conducted in consideration of these factors.
Internal audits are conducted to confirm that the objectives of introducing the ISMS are continuously fulfilled, i.e., that ISMS is effective, which will lead to the ongoing maintenance and advancement of business.
Effectiveness is defined as “the extent to which planned activities are implemented and intended results are achieved,” and proper planning and appropriate implementation lead to effective results.
In other words, it is the “integration of the ISMS and business operations.”
Here, we will cover the “shift of focus from auditing conformity to auditing effectiveness.”
1. The problems with ISMS internal audits
― How conformity audits tend to nitpick ―
Standards vs. facts
ISMS internal auditing is activities to check whether ISMS operations―the various tasks in day-to-day business―are in conformity with information security-related standards and in-house regulations and are effective in terms of security.
However, auditors often cannot determine whether their findings are of conformity or nonconformity to the standards, because they:
- Overlook the facts at hand
- Do not know how to distinguish the facts
- Cannot decide whether the findings are important or not
- Do not know what audit criteria should be applied to specific findings
- Do not understand the purpose of the audit criteria
- Inflexibly apply audit criteria to all items
- Interpret audit criteria as they wish
The auditors may not notice any risks, or they might hesitate to point them out for correction even if noticed if they have no knowledge of the business operations of the organizations being audited and do not know the significance of their findings.
While the purpose of auditing is to determine whether or not the findings meet the audit criteria, if the auditors cannot identify the findings or are not aware of the purpose of the audit criteria, the true goal of the auditing will not be achieved even if items to correct are pointed out.
Recognizing the essentials
An auditor might decide that the facts noticed do not meet certain criteria based on their findings, and demand that the corrective action be taken by stating,
“This fact does not conform to this criteria. Please make corrections.”
In this case, however, most corrective actions only remove the visible events that are pointed out, without realizing the primary causes of various events.
Repeatedly pointing out items and correcting them leads to the occurrence of similar events with differing causes, and the auditor falls into a repetitive cycle of pointing them out each time again and again like a game of whack-a-mole.
For example, not keeping some necessary records may be caused by a lack of defined work procedures or unclear roles. Records being neglected may be due to a lack of education necessary to make employees aware of the importance of keeping records in the first place.
If both the auditor and the audited organization do not recognize the primary causes of the problem, the necessary corrections cannot be made.
As the ISMS is put into greater use, regulations are better implemented, and management of information assets is done better, more measures will be taken to address that which is easily visible each time there is an audit, and eventually issues will only be discovered in audits by nitpicking.
So, what are essential causes of the following items pointed out?
- Some records were not signed off by the manager.
- Due to revision of the regulations, some inconsistent terms were found in some sections of other related regulations.
- Follow-up has not been completed for employees who have yet to receive required education and training.
- Documents were left on printers or fax machines.
- Some information assets that should have been disposed of remained even after the disposal date.
- Documents were piled up on the desks of employees who were absent.
- Some of the items to be input for management review have been left unreported for over a year.
Auditors cannot help to nitpick if they only focus on conformity in audits. Can we judge a decline in the number of issues pointed out in audits to mean that the information security level has improved?
Questions raised by the management team
For information security, the return on investment is unclear. Much costs are incurred for personnel expenses in tasks such as training of many internal auditors, implementation of risk assessments, internal audits, and management reviews.
But is the company’s information security truly effective? It is natural for such questions to arise.
- If no problems are pointed out in the internal audit, does it mean that our information security system is perfect?
- Have the auditors improved their abilities by carrying out yearly audits?
- The management review process reported that no incidents or accidents took place, but might there be some accidents that were not overlooked or covered up?
- The amount of investment in information security cannot be taken lightly, but is the company’s ISMS effective?
For information security, the return on investment is unclear.
Shift of focus from conformity to effectiveness
Assuming that the acceptable risk level is constant, the number of compliance violations identified in an audit will decrease over time and conformity-related risks will no longer exceed the acceptable level. The items pointed out, however, will simply be the results of nitpicking.
On the other hand, if anti-risk measures are left as they are, they will not be able to respond to increased risk due to changes in the situation, making it impossible to ensure the appropriate condition. The shift of focus to effectiveness is meant to ensure that anti-risk measures lead to an acceptable level of risk.
The following figure illustrates the shift of focus from conformity to effectiveness.
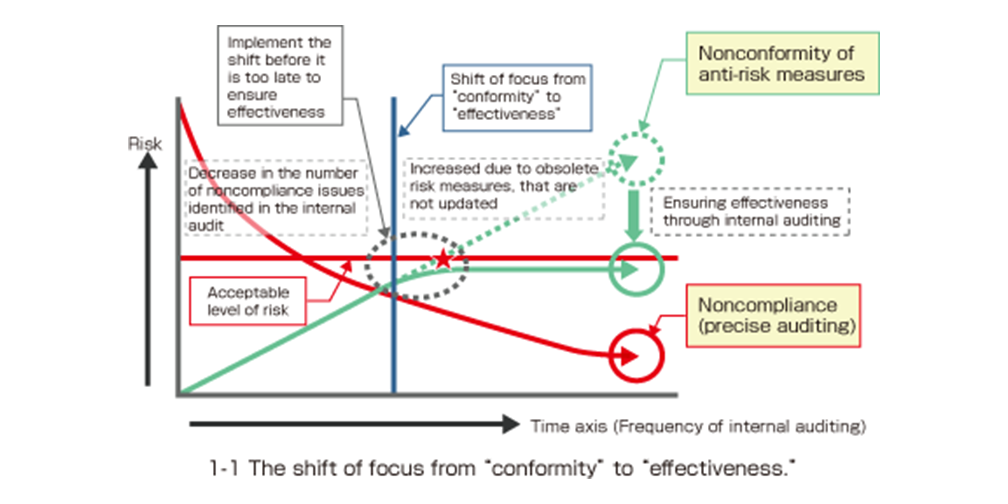
If effectiveness of internal auditing cannot be maintained, measures will not be taken until invisible risks become apparent in actual incidents.
Importance of findings
Auditors may not be intimately familiar with the business operations of the departments they audit. It would be ideal for each auditor to examine the business operations of the audited department, the department’s key operations, and the security of related information assets, and to make a focused auditing plan.
In reality, however, auditors tend to perform audits in a short amount of time in order to avoid interfering with business operations, so the audits tend to be superficial without details being sufficiently examined.
The audited departments, however, deepen their understanding of internal audits in the course of repeated executions of the PDCA* cycle for the ISMS, and they will no longer be satisfied with items pointed out from superficial audits. If organizations are not satisfied with things such as explanations of why items are being pointed out, to what extent corrections are needed, whether it is necessary to consider cost effectiveness, they may feel that auditors are just disturbing their business operations with ineffective and inappropriate auditing.
*PDCA: A management cycle in which the Plan, Do, Check, and Act processes are performed in sequence.
In pointing out any audit findings, auditors therefore need to clearly show the potential risks associated with the business operations of the audited organization and explain to gain the organization’s understanding of what incidents might take place if issues are left unresolved. If this process is appropriately conducted, the audited department will be satisfied that the auditors have pointed out valid issues regarding risk countermeasures.
In-house rules naturally should be adhered to, and even minor violations should not be ignored. Items needing improvement that are low-risk but should not be neglected should also be included in audit findings, depending on the degree of risk.
Auditors who do not understand the actual business operations of the audited organizations tend to judge findings to all be equally important; however, they will be able to judge the actual importance of the findings if they understand the features of the organizations they audit.
The next part will be “2. You cannot deal with what you cannot see ― Visualizing information security risks―”