- Home
- Products & Services
- Security of RICOH Products and Services
- Security for Ricoh Multifunction Printers
- Security Threats and Countermeasures
Security Threats and Countermeasures
Wondering if your devices are vulnerable?
Security threats are no longer limited to personal computers, servers or networks. Printing devices — even basic laser printers — need countermeasures against a diverse range of threats. As multifunction printers have evolved into true information terminals, they have become core IT assets in their own right. The computing capability of what have been traditionally categorized as “Printer/Copiers” has grown, but so too have potential threats.
Simply hoping you don’t get hit is not the answer. Superior technology, commitment and know-how are essential. As a forerunner in the field of security countermeasures of multifunction printers, Ricoh addresses every conceivable security threat:
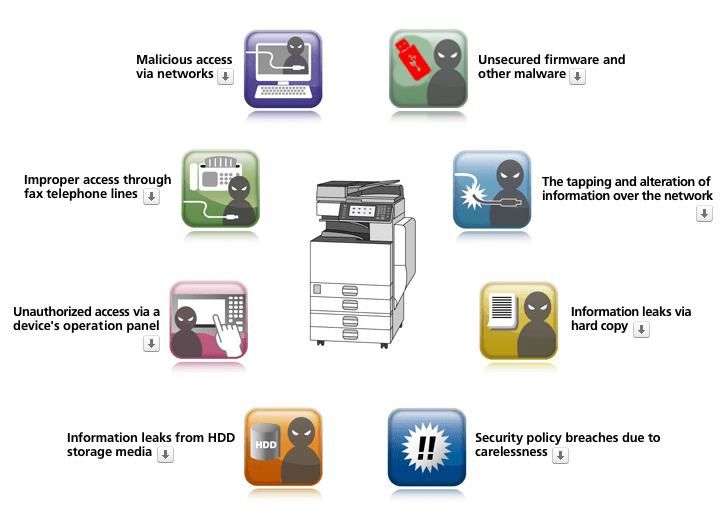
- Security threats in offices
- Security threats in offices
- unauthorized access via telephone lines
- tapping and alteration of information over the network
- unauthorized access via the operator panel
- information leaks via storage media
- information leaks via hard copies
- information leaks due to carelessness
Unsecured firmware and other malware

If a multifucntion printer's or printer’s built-in software — also known as firmware — is altered or compromised, that device can then be used as a method of intrusion into the corporate network, as a means to damage the device or as a platform for other malicious purposes. Ricoh-designed devices are built using a Ricoh-only Trusted Platform Module (TPM) and are designed to not boot up if the firmware has been compromised.
In addition to the firmware, many multifunction printers support the installation of applications which, if allowed to run, could allow an attacker access to the device. To protect against malicious code, Ricoh's multifunction products will only allow an application to be installed if it incldues a valid Ricoh digital signature.
Malicious access via networks

In an increasingly connected modern world, the number of possible points of entry for a malicious attacker also increase. While multifunction printers can be discovered over the network, features such as user authentication and filtering help reduce the risk of information leaks via networks by preventing an intruder from accessing internal features.
Improper access through fax telephone lines

Enabling a device’s fax feature may mean connecting it to the outside via a telephone line — which means that blocking potential unauthorized access via the fax line is critical. Ricoh embedded software is designed to only process appropriate types of data (i.e. fax data) and send that data directly to the proper functions within the device. Because only fax data can be received from the fax line, the potential for unauthorized access from the fax line to the network or to programs inside the device is eliminated.
The tapping and alteration of information over the network

Multifunction printers exchange critical information with computers and servers over networks. If left unprotected, this information is at risk of alteration by those with malicious intent who would tap into the network. Ricoh multifunction printers and technologies offer features that can help protect against unauthorized access via networks.
Unauthorized access via a device’s operation panel

Multifunction printers in an office environment are exposed to security risks of unauthorized access to information via the operator panel. Many cases of information leaks are reportedly committed by insiders. To reduce these risks, Ricoh's multifunction printers include user authentication features so that specific access privileges can be set up for individual users. It is important to properly manage and run devices without letting users access the information and functions they do not need.
Information leaks from HDD storage media

Multifunction printers have a built-in storage device, such as a hard disk drive, for strong information such as address books and documents. The hard disk drive may also contain temporary copies of information scheduled for transmission, reception and printing. Using Ricoh's data encryption and data overwrite features can reduce the risks of information leakage, even if the storage device were physically removed from the device.
Information leaks via hard copy

A document left on the tray of a multifunction printer could be read or taken by anyone. Whether it was taken deliberately or accidentally, this is an information leakage risk. To help protect your information, Ricoh multifunction products include user authentication and locked printing features.
Security policy breaches due to carelessness

Information could be leaked by accidentally sendng a fax to an incorrect address, or making too many copies of a document and leaving them behind. Ricoh's multifunction printers feature functions that can help minimize the risk of information leaks due to carelessness.