- Home
- TAMAGO Labs.
- RICOH TAMAGO Tombolo
RICOH TAMAGO Tombolo

Do you have a problem like this?
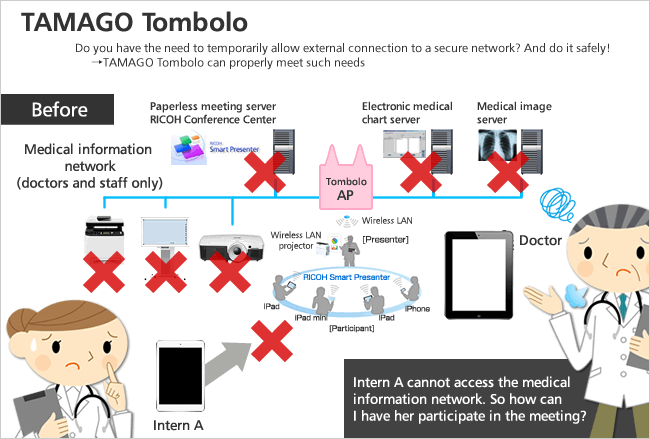
At TAMAGO, we developed TAMAGO Presenter, the predecessor of Smart Presenter. At that time, we decided to try holding a paperless meeting, and as participants we had employees plus two people from outside the company, in this case customers. The employees were able to access the company’s wireless LAN and conveniently use a variety of devices and systems. However, even though they had iPads, the customers could not access the company’s internal network so they could not participate in the paperless meeting, and we ended up having to give them printed versions of the materials and share projector screen images with them. For the employee presentations, the meeting could proceed using smart projector displays done via wireless LAN, but when the customers needed to present information, they could not connect to the wireless LAN so their presentations were made by connecting their iPads via a legacy VGA cable (for connecting a PC to video devices). On top of that, an error occurred, and the employees also ended up going back to the old way of doing things, i.e., connecting to the projector via VGA cable. So, despite the fact that there was an available system set up based on the premise of a wireless-LAN compatible projector, printer, and network, only certain people could use that system. It was an unfortunate waste of resources.
We wondered whether there wasn’t some way we could solve these kinds of network issues that are found in many situations where people are trying out innovative work styles. From this problem, TAMAGO Tombolo was born.
What is a "tombolo"?
Tombolo is not a term most people are familiar with. It is a geographical term that refers to a sand bar connected to land. Relatively well known examples that you may know include the islands of Enoshima in Japan’s Kanagawa Prefecture and Mont Saint-Michel in France. The tombolo is what connects these islands to the mainland. The tombolo phenomenon occurs when an island normally separated from the mainland by sea becomes connected to it by land rising above the surface at low tide. We developed Tombolo in response to the question: For networks, can we create a mechanism that connects when connection is necessary and that separates when connection is not necessary?

<Photo of land-tied island: Mont Saint-Michel>
Mechanism for external connection to a network using TAMAGO Tombolo
The mechanism has three very simple steps.
STEP1: In accordance with the instructions of the host (that invited the guest), have the guest terminal connect to the Wi-Fi network that is the network entry point. (The operation is simple! It can be done using only standard OS functions and a Web browser.)
STEP2: The host selects the network connection device/service used by the guest. (Tombolo is set up so that if this is not done, "it is only possible to reach the entrance" !)
STEP3: Just that easy, now the host and guest can collaborate using the devices of each.
The reasons that TAMAGO Tombolo can provide a defined level of safety and security
The basic safety and security framework of the Tombolo system is made up of five elements.
(1) It is possible to provide a Wi-Fi setting and connection environment that is safe for the guest.
The secure communications of the guest terminal are guaranteed using wireless LAN access point encryption/authentication that operates using the WPA2 personal security method recommended by the Wi-Fi Alliance, an industry organization that promotes the spread of wireless LAN use.
(2) Since the host that invited the guest does the authentication on the spot, it is possible to have the guest terminal do the Wi-Fi settings and connection.
The action of the guest doing the Wi-Fi setup is not possible through the solo operations of the guest. The Wi-Fi settings and connection are only possible as a result of authentication operations of approved persons present at that place. In the authentication operations, difficult network settings and operations are not necessary as the authentication can be done with a simple and intuitive user interface that uses a Web browser.
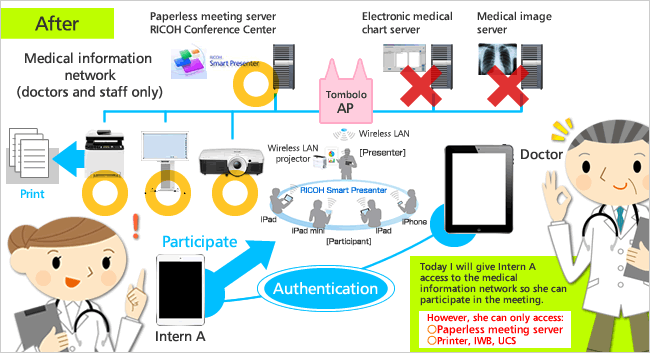
(3) By having the host that invited the guest carry out the changes to the access control settings in a safe and intuitive manner, it is possible to give the guest terminal access permission only for designated devices and services connected to the network.
It is a problem if the guest terminal can access the entire network after it is connected. It is possible for the host that invited the guest to control at the network communication level the network devices and services available for use. From among the network-connected devices and services set up as usable beforehand, it is possible to easily select those to which the guest terminal is to be permitted access.
Here also, the access control rule settings do not require difficult network settings and operations. The fact that the settings can be done with a simple and intuitive user interface helps to prevent the giving of unnecessary access permission through operation errors.
(4) The usable network-connected devices and services can be defined only by the operator with administrative authority so operations are also safe for the core-network operator.
The devices and services to which the host that invited the guest can permit access must remain within the scope defined by the core-network operator. The system operator also does not have to worry since it is possible to guarantee that access will be limited to the managed scope so the guest will not be allowed unlimited core network use.
(5) Since the Wi-Fi network /access control rules generated are only temporary, the host that invited the guest can use them safely and safe operations are also possible for the core-network operator.
If a guest who has already connected once were to be able to again connect to the Wi-Fi network and access network resources using the same settings even after the end of the collaborative work, there would be a danger that prohibited network use could occur. By having the host that invited the guest carry out an explicit operation to end guest access or by forcibly ending guest access using an expiration date setting, the temporary Wi-Fi network and access capability will end/expire, thereby guaranteeing safety. The next time a Wi-Fi network is generated, SSID and PSK will again be randomly generated so there is no chance of a sudden connection occurring with the previous settings.
These five elements can be freely combined for flexible operations tailored to the usage situation and scale.
For example, the following actions are also possible:
"Omit (2) and open the Wi-Fi setting/connection authentication operations to the guest. (However, this only covers that Wi-Fi connection so if the host does not give permission to go beyond that, nothing can be done.)"
"For a small-scale network, operate with the same authority level both for the host that invited the guest and for the core-network operator."
The following usage example exists.
Last year, we exhibited at the Joint Conference on Medical Informatics. Data containing personal information (electronic medical chart information and medical images) is handled in medical settings so network security is strictly managed in order to prevent data leaks and unauthorized access. With the improvement and spread of medical technology, however, it has become necessary for medical students and interns to also access clinical information. For our exhibit, we built a demo system that showed how TAMAGO Tombolo could be used to enable interns to (with the permission of a doctor with network administrative authority) temporarily access a hospital’s internal network when necessary to participate in paperless meetings and also print materials from an MFP in the same environment.

For customers with an interest in Tombolo
Unlike other TAMAGO products created up to now, TAMAGO Tombolo is not an iOS application. It cannot be just downloaded and used by customers. This being the case, at RICOH we have established a meeting space with TAMAGO Tombolo installed. There customers can actually experience TAMAGO Tombolo, discuss their problems with us, and consider how we can move forward together to solve those problems. TAMAGO Tombolo is still at the TAMAGO stage. We hope to further develop it along with our customers. If you are interested, please contact us at the email address below. We will arrange a meeting.
At TAMAGO, we are developing Tombolo together with our customers. We hope you will collaborate with us.
Some anticipated usage situations
Here we explain some of the TAMAGO Tombolo usage scenes anticipated by TAMAGO.
Scene 1: Install TAMAGO Tombolo in a meeting room and connect it to an intranet
- Install TAMAGO Tombolo in a meeting room and connect it to an intranet.
Scene 2: Install TAMAGO Tombolo in a meeting room and connect it to a standalone LAN
- After the customer’s terminal is connected to the local area network (LAN) using TAMAGO Tombolo, the customer can use the projector and printer in the meeting room.
Scene 3: Install TAMAGO Tombolo in a co-working space
- After the customer’s terminal is connected to an intranet using TAMAGO Tombolo, the customer can have internet access, etc.
To use Tombolo
-
TAMAGO Tombolo prerequisites in order to connect to a network via TAMAGO Tombolo (iOS/Windows/Android)
- iOS (8.0 or later): Safari
- Windows, Android: The terminal needs to be able to use a wireless LAN and push-button-type WPS (Wi-Fi Protected Setup)
- After connecting to a network via TAMAGO Tombolo, there may be cases where it is necessary to have the application or software for what the customer is to do.
For example, when using the “RICOH Smart Presenter” paperless meeting solution on an iOS device, it is necessary to have the RICOH Smart Presenter application. - Concerning RICOH Smart Presenter, see here (http://www.ricoh.com/software/smartpresenter/).

Please contact us via e-mail about system trouble or your questions about this application.