
- Home
- Information Security
- Information security at the Ricoh Group
- ISMS Certification / Cybersecurity maturity assessment
- Ricoh Family Group Information Security Measures (RFG ISMeasures)
Ricoh Family Group Information Security Measures (RFG ISMeasures)

The Ricoh Group established common standards in March 2007 and has been promoting the full-scale deployment and entrenchment of those common standards at our Group companies since April 2007. With these common standards, we aim to continuously improve the information security response level of each company and further bolster the foundation for providing new value to customers.
Aiming to raise the level of security for the Group as a whole
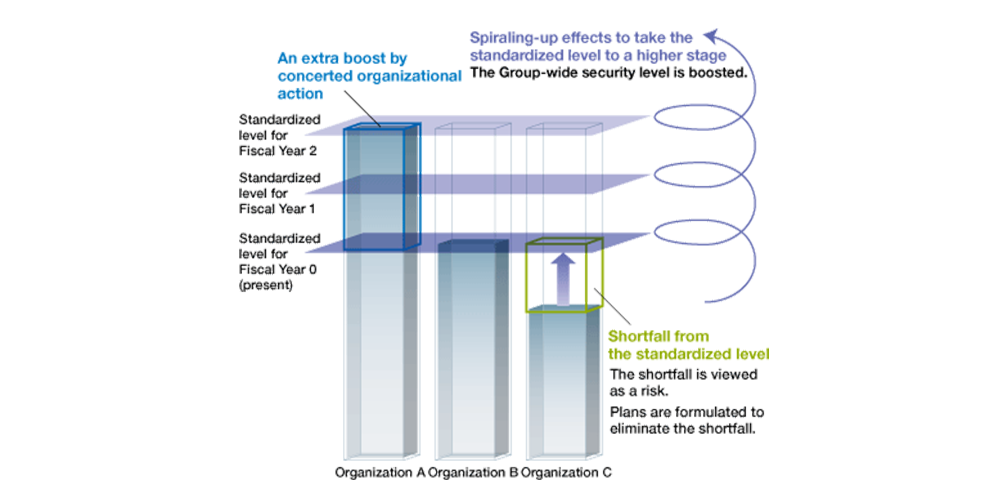
In order for the Ricoh Group to fulfill our corporate social responsibility and enhance our corporate value through information security initiatives, it is important for us to make security levels be common so as to raise the information security of each company above a certain level, transcending the boundaries between group companies.
Even within the same corporate group, there are many differences in size and corporate culture of the individual companies, and each company has a wide range of operations, which may include research, development, design, production, sales, and service. There also tend to be differences in the level of information security addressed on an individual basis. The Ricoh Group has recognized the need for common standard that would serve as a unified security policy for the entire Group in order to resolve these various problems and make the Group ISMS, which serves as the foundation for information security activities, even more effective. Additionally, the ISO/IEC 27001 international standard does not specify the extent to which individual safety measures should be implemented, so specific implementation standards were necessary. In response to the requirements of the international standard, we began studying standards for implementing information security according to the degree of risk in December 2005, established the Ricoh Group Standards (RGS) in March 2007, and have been promoting the full-scale deployment and adoption those at our Group companies since April 2007.
Common standards according to information asset importance
The purpose of establishing common standards and disseminating them across the Group is to make information security practiced by individual companies common and raise that to a certain level, and to trigger spiraling-up actions to continuously raise this level. To achieve this, the ISMS framework is used to take inventory of the information assets of Group companies, conduct risk analysis of each asset, identify weaknesses, and take appropriate management measures against those.
From this perspective, the RFG ISMeasures specify standards for the handling of each type of information asset. They are broadly classified into information content, physical assets, IT systems, services, and cooperative organizations, each with two stages of checks, “required measures” and “recommended measures,” depending on the degree of business importance.
Image of spiraling-up common levels
Policy formulation according to the worksite based on common standards
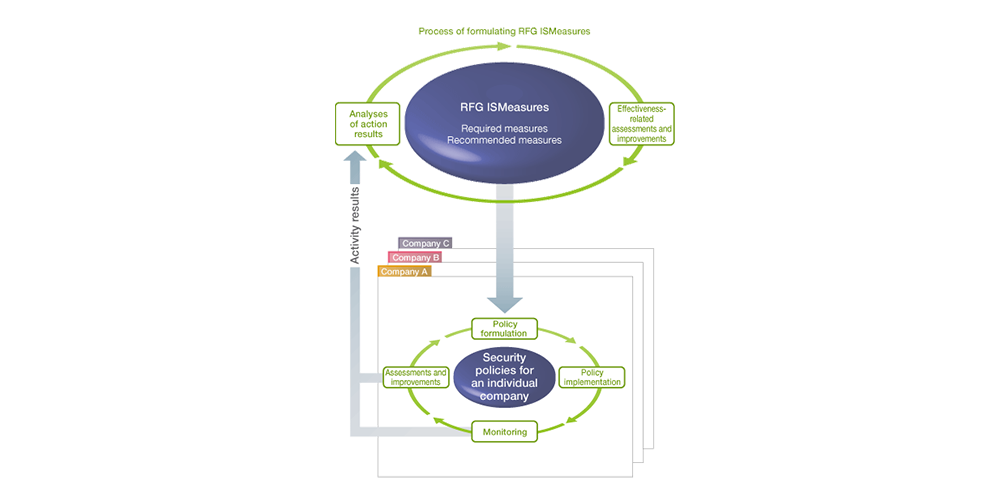
Required measures must be implemented across the Group. The person responsible for information asset management at each worksite compares the requirements and security level applied for a specific information asset against its present level of security management, assesses the risks while checking whether a shortfall exists, and takes management measures to address those risks. Recommended measures may be taken at the discretion of each worksite to suit its task characteristics. Those can be compared in the same way to determine the need for risk response according to the characteristics of each worksite. And if there are additional items to be observed according to the functions, features, and circumstances of the organization, unique management measures can also be added. This approach allows RFG ISMeasures to be optimized to suit individual worksites, which results in them being established as security policies unique to each company. These security policies are integrated into day-to-day business operations, and they are carried out and refined by worksite managers in the course of the PDCA (plan-do-check-act) cycle of day-to-day management.
In addition to the handling of such information assets, the state of the management system is also assessed in order to review the management level administered in the organization, enabling confirmation of the proper functioning of the PDCA cycle. Dedicated tools are also available to facilitate these risk assessment procedures.
Risk assessments by individual companies based on common standards
Achieving simplified risk assessment
A feature of information security management based on common standards is that simplified risk assessment techniques based on common standards are introduced. This has made risk assessment and response simpler than before for worksite managers who manage information assets on the front lines of operations. And a mechanism has been put in place whereby a third party can check conformity and effectiveness through internal and external audits. In this way, the control division of the head office collects the results of security activities by Group companies and summarizes these results for use in future assessment and improvement of common standards. The common standards are updated in accordance with changes in the external environment and the Ricoh Group’s situation, and the security level throughout the Group is raised by spiraling-up actions.